Actualización: Enigmail 2.0 y Thunderbird 52.7.0 (así como versiones posteriores)
ya cuentan con mitigaciones. Los usuarios de cualquiera de estos clientes (o de otros afectados) deberían instalar dichas versiones o usar un cliente protegido como los mostrados en las tablas de la noticia. Gracias por el aviso, STeNYaK.
Noticia original: Hace aproximadamente un día saltó la alarma: la Electronic Frontier Foundation (EFF)
alertaba de que los sistemas de cifrado
OpenPGP y
S/MIME estaban afectadas por graves vulnerabilidades. Algo sumamente grave si se considera que PGP es desde su lanzamiento en 1991 una de las soluciones criptográficas de uso general más seguras, y por ende también una de las más extendidas. Ahora han sido divulgados todos los detalles al respecto.
Las vulnerabilidades, que han sido descubiertas por un grupo de investigadores europeos, aparecen detalladas en el sitio
EFAIL.de, donde se ha colgado toda la documentación necesaria junto a una prueba de concepto para demostrar la validez. Hasta ahora todo lo que había era una notificación de riesgo, pero con la publicación de los datos queda certificado que tanto OpenPGP como S/MIME ya no son tan resistentes como se pensaba (S/MIME, de hecho, parece estar afectada por un mayor número de agujeros de seguridad).
Según los investigadores, EFAIL explota varias vulnerabilidades en los estándares OpenPGP y S/MIME para desvelar los contenidos de un correo electrónico en texto plano. Para ello abusa contenido activo de correos electrónicos en HTML (como los utilizados para cargar imágenes externas) para extraer texto plano desde las direcciones en cuestión. Para crear los canales de exfiltración necesarios primero es necesario acceder a los correos electrónicos, ya sea monitorizando el tráfico de la red, accediendo de los servidores o vulnerando la seguridad de la cuenta y/o el ordenador del usuario espiado.
A continuación, detallan los investigadores, el atacante modifica un e-mail cifrado de una forma concreta y lo envía a la víctima. El cliente de correo del usuario atacado descifra el mensaje y carga el contenido externo, momento en el cual se realiza la exfiltración del mensaje en texto plano al atacante.
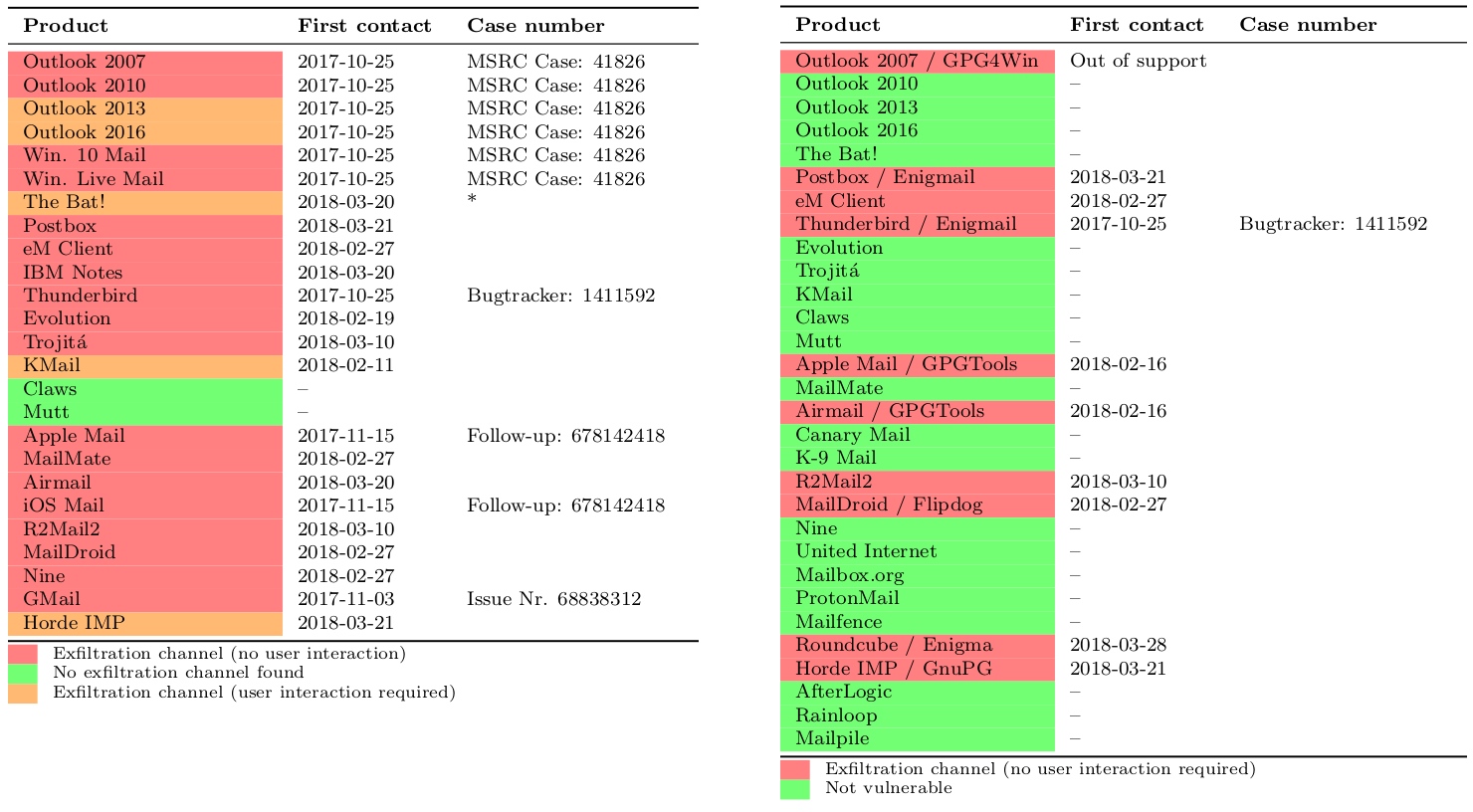 Clientes S/MIME y OpenPGP (respectivamente) afectados por los fallos.
Clientes S/MIME y OpenPGP (respectivamente) afectados por los fallos.De acuerdo con los expertos de EFAIL, los canales de exfiltración existen en 25 de los 35 clientes de correo electrónico S/MIME y en 10 de los 28 clientes con OpenPGP probados durante la investigación. Otros son inmunes al no permitir que correos maliciosos se aprovechen del comportamiento indefinido de los estándares que hace posibles los ataques.
Dado el que PGP es utilizado principalmente por personas que por su trabajo o situación personal están potencialmente expuestas a la intercepción de sus mensajes (aunque la prudencia señala que este tipo de medidas nunca están de más en ningún caso), desde la EFF se recomienda dejar de utilizar ambas tecnologías y pasarse al menos temporalmente a otras formas de comunicación segura.
Según señala la EFF, las vulnerabilidades podrían ser resueltas actualizando los protocolos y el software vulnerable. Esto, en cualquier caso, no será algo inmediato. Algunos parches ya han comenzado a ser distribuidos, pero como bien indica la fundación, "tendrá que pasar un tiempo para que cada uno de los usuarios de todos los programas afectados estén al día, y aún más antes de que los estándares sean actualizados". Los desarrolladores de OpenPGP ya están trabajando en ello.
Fuente: Efail 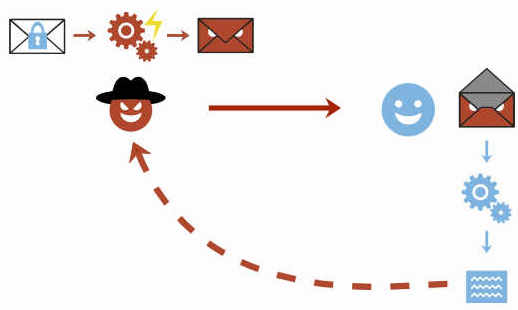
 Clientes S/MIME y OpenPGP (respectivamente) afectados por los fallos.
Clientes S/MIME y OpenPGP (respectivamente) afectados por los fallos.
![sonrisa [sonrisa]](/images/smilies/nuevos/risa_ani1.gif)
